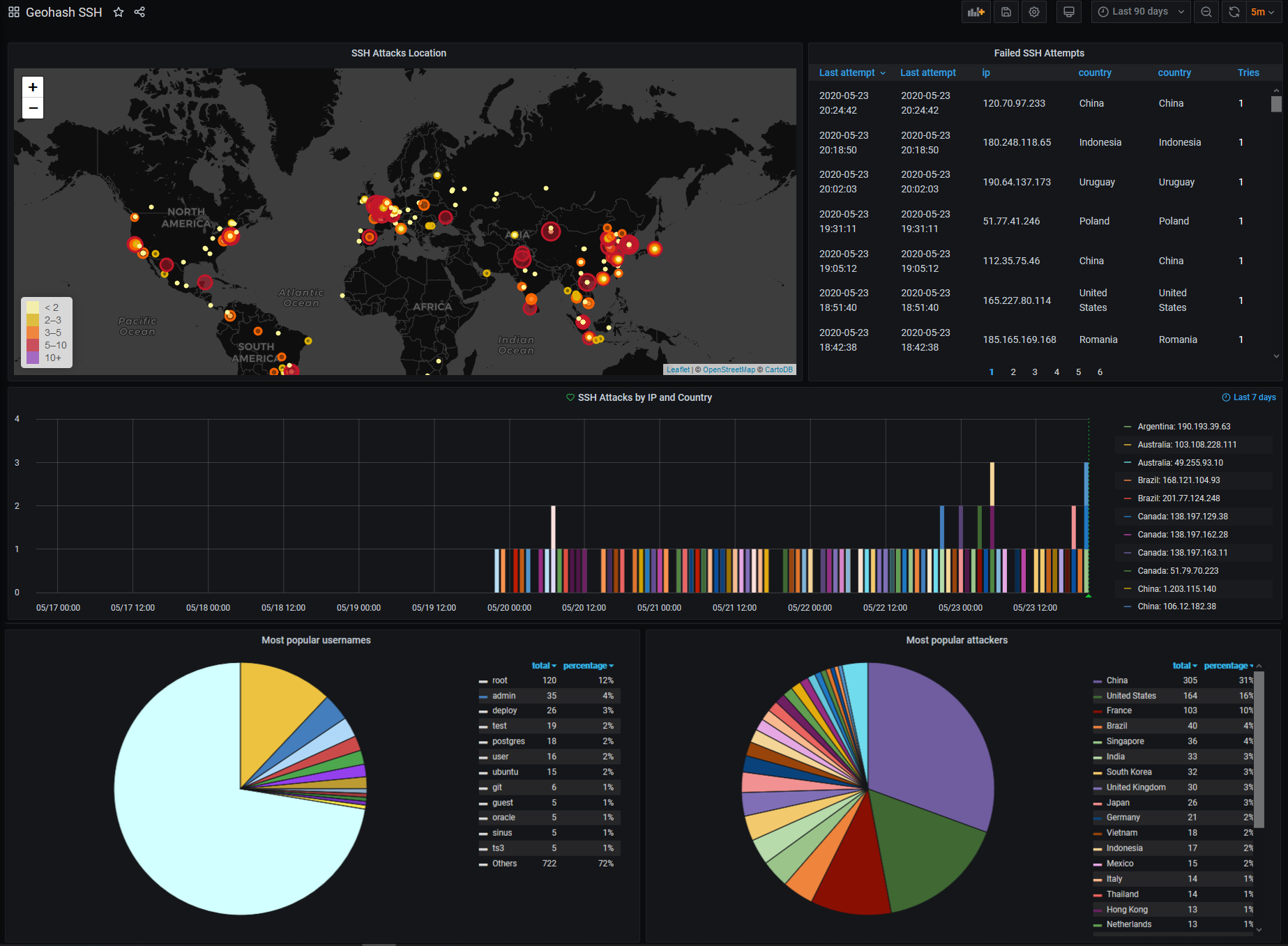
How to Monitor and Visualize Failed SSH Access Attempts to Amazon EC2 Linux Instances | AWS Security Blog
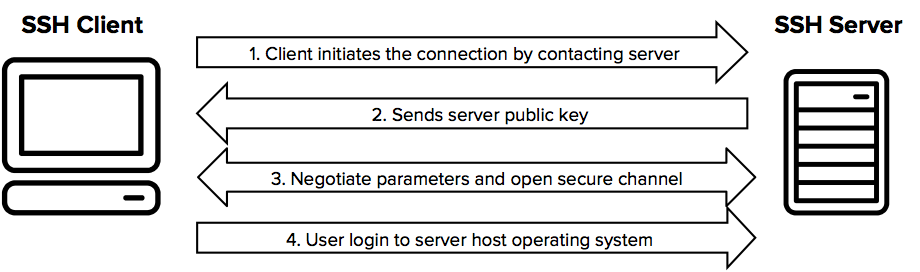
SSH protocol is the standard for strong authentication, secure connection, and encrypted file transfers. We developed it.

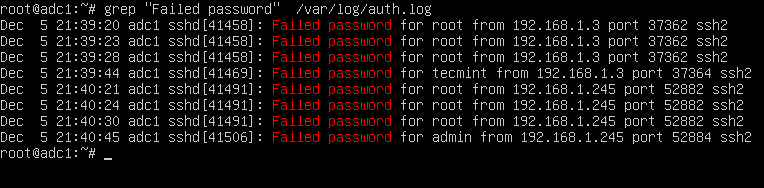
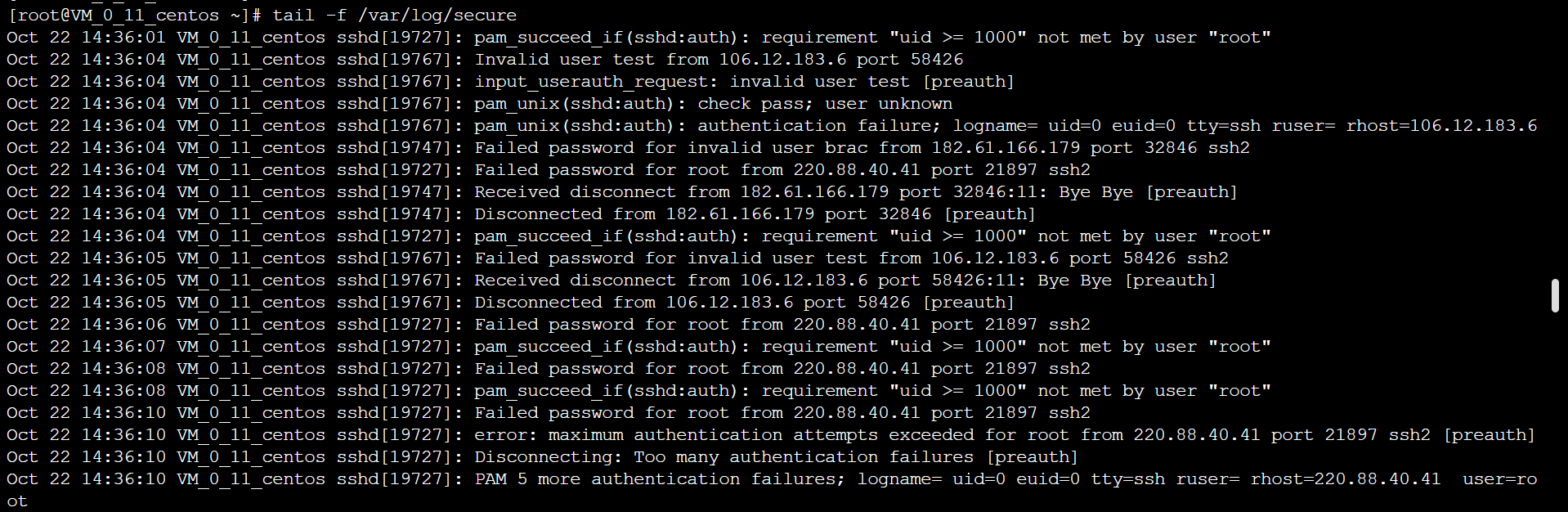
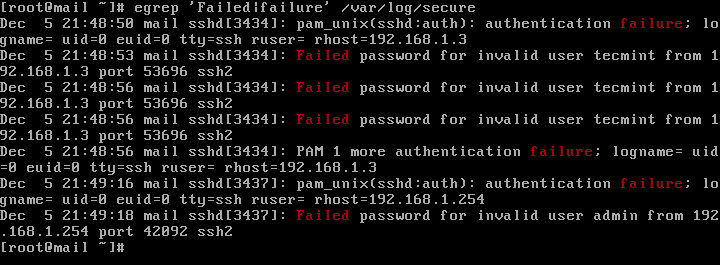
Yet another ssh brute force attack and how to protect against it with iptables and sshguard – The GNU of Life, the Universe and Everything

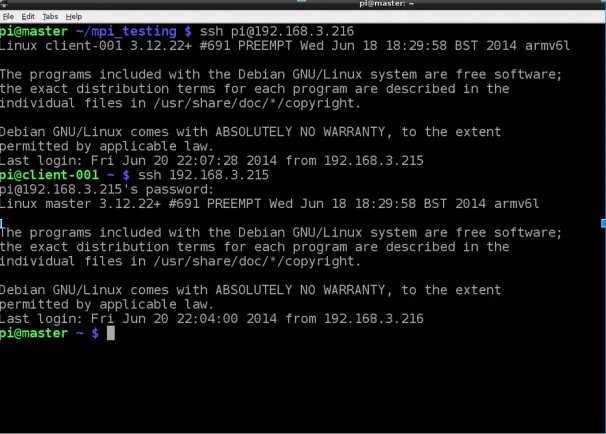
Is it possible to have 2 ports open on SSH with 2 different authentication schemes? - Unix & Linux Stack Exchange